Vulnerability Management
Endpoint Security Solutions
The Host-Based Security System Center is a data monitoring and analytics capability that provides administrators and select teams access to real-time asset status and reports, plus centralized configuration and management tools that enable your organization to react quickly.
The Endpoint Security suite of products is designed to actively protect your network assets from theft, manipulation, or loss from internal or external threats. The centrally-managed server allows staff to deploy, update, configure, and manage the suite of products remotely and discreetly across your network.
Assured Compliance Assessment Solution
The Assured Compliance Assessment Solution (ACAS) automates configuration (compliance) assessments as well as network discovery and vulnerability screening. The major toolkit required by the DoD is included in the solution, along with Tenable.sc (formerly SecurityCenter) and Nessus services.
Command Cyber Readiness Inspections
Our team of knowledgeable CCRI compliance specialists provides invaluable insight into what it takes to bring compliance to command-level enterprise networks as well as small business networks. Although we have helped hundreds of organizations go from failing to receiving Excellent and Outstanding ratings, we think our work is guided by a much larger objective. We work together with you to strengthen the security, resiliency, and readiness of your organization.
A Broad Range of Command Cybersecurity Readiness Inspection (CCRI) Services
- CCRI Phase IV Grading
- CND Directives Guidance
- Vulnerability Management
- CCRI Tool Configuration
- Insider Threat Mitigation
- McAfee ePO Engineering
- Endpoint Deployment
- ACAS Security Center
- Nessus Engineering
- Network Perimeter
- Nessus Engineering
- Infrastructure Hardening
- Wireless Discovery
- Wireless Controller
- Program Managed (PM) System Evaluations
- Endpoint Assessments
- Blackberry Mobility Configuration Services
- Active Directory
- Exchange Compliance
- UNIX | RHEL Security Compliance
- Domain Naming System (DNS) Security Services
- Database Security Compliance
- Web Security Compliance
- Cross-Domain Solutions (CDS) Consulting
- REL Implementations & Architecture Reviews
- MS Workstation Hardening
- Physical Security
Risk Management Framework
Department of Defense Agencies
To obtain a DoD Authority to Operate (ATO), do you have to evaluate your information systems in accordance with DoD RMF standards? We can assist you in evaluating your information systems in accordance with DoD RMF requirements with our DoD RMF certification and accreditation service. We offer RMF help to the Department of Defense agencies using NIST Special Publication (SP) 800-53, the RMF framework’s six stages (see below), and our wealth of knowledge.
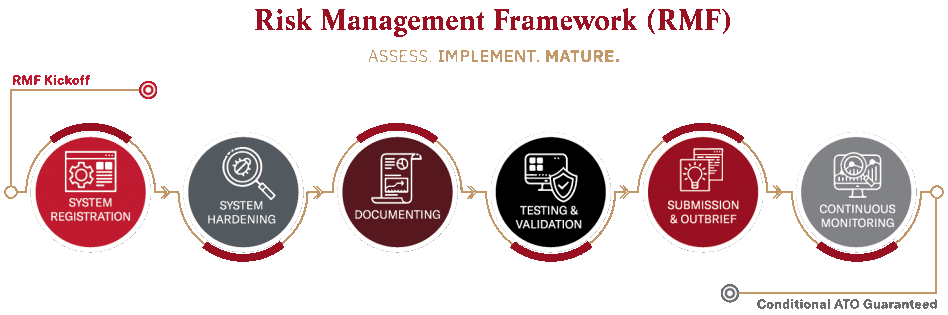
Risk Management Framework Services
- Security Technical Implementation Guide (STIG) evaluations, in-depth Application Security assessments, and System Hardening
- Complete documentation (as needed, including POA&Ms, & SSPs)
- Artifact creation & testing
- eMASS uploads and management
- Engineering Scans ACAS scans
- Vulnerability assessments
- Vulnerability scans and configuration
Your software, architectures, cloud migrations, and other tools will be engineered in a cost-effective manner by our Subject Matter Experts (SMEs) to support the development of secure systems. We efficiently leverage your current assets and licenses to maximize and improve cybersecurity across your entire enterprise.
Enterprise directories and email Solutions
The mainstay of company communications and the most exposed enterprise application is email. NoMa Solutions offers two-tier, 24×7 E-mail technical and Help Desk support, as well as a full spectrum of hardware and software maintenance support, in order to support enterprise mail and online services. We provide administration of the present systems as well as engineering designs for enhancing the Enterprise mail architecture as part of our support for Enterprise Mail. NoMa Solutions approach to improving enterprise email performance entails working with the customer to troubleshoot email issues and frequently assisting other sub-organizations and contractors when the issue falls within their purview.

